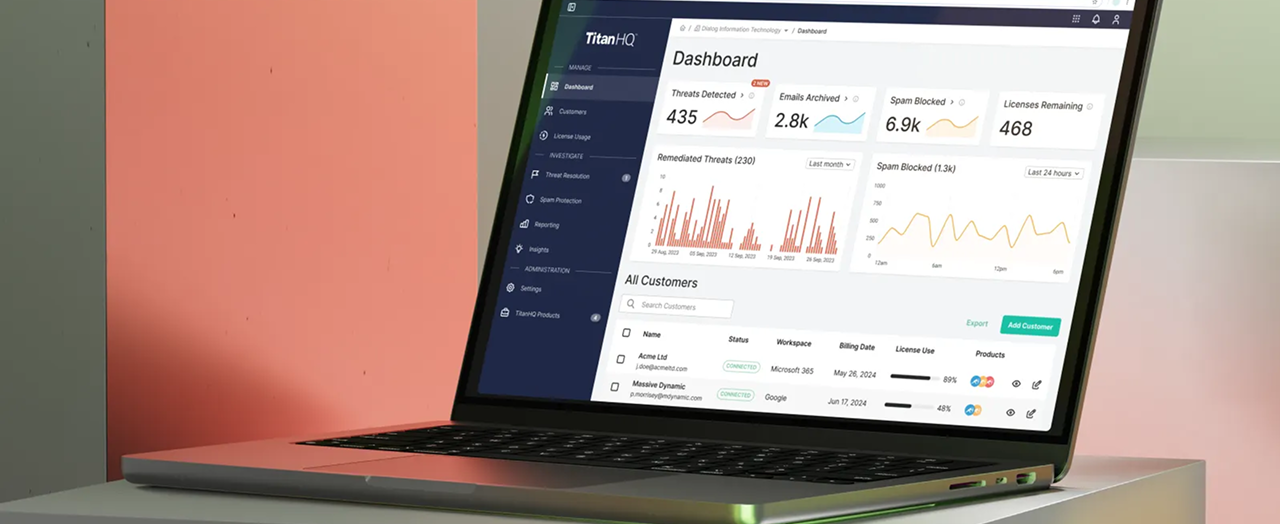

PhishTitan Threat Detection Platform
The problem
Key goals:
- Increase threat detection accuracy and reduce false positives
- Create a unified platform that consolidates threat intelligence from multiple sources
- Build an intuitive interface that makes complex threat data accessible and actionable
Process
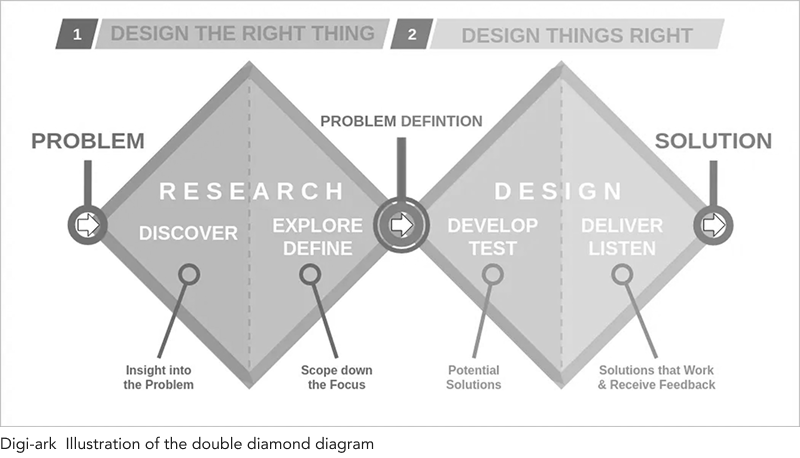
Following the Double Diamond methodology, we moved through four key phases: Discover (Research, Synthesis), Define (Ideation), Develop (Prototyping), and Deliver (Testing, Implementation). This structured approach ensured we understood user needs deeply before designing solutions.
Discover
User Research
- Conducted interviews with security analysts, IT administrators, and security managers
- Observed users working with existing threat detection tools
- Analyzed support tickets and user feedback from current platforms
- Reviewed industry reports and threat intelligence trends
Insights
- Security teams are overwhelmed by alert fatigue and need better prioritization
- Users want contextual information that explains why something is a threat
- Threat intelligence needs to be actionable, not just informative
- Teams need to collaborate effectively when responding to incidents
Competitive Analysis
- Analyzed leading threat detection platforms and their user interfaces
- Identified gaps in visualization and data presentation
- Studied how competitors handle threat intelligence and reporting
Findings
- Most platforms focus on technical details but lack user-friendly visualizations
- Threat data is often presented in isolation without context
- Workflow integration is limited, requiring users to switch between multiple tools
Opportunity
- Create a platform that combines comprehensive threat intelligence with intuitive design
- Provide clear visualizations that help users understand threat patterns and trends
- Enable faster decision-making through contextual information and actionable insights
Define
We mapped the ecosystem of users, their workflows, and information needs. This included creating user personas, mapping user flows for key tasks like threat investigation and response, and defining the information architecture that would support these workflows.
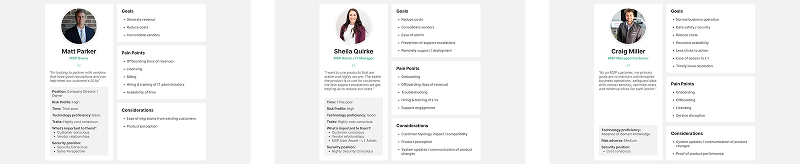
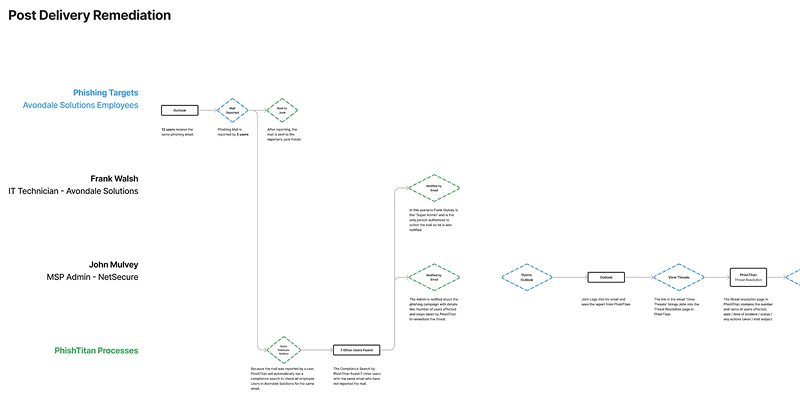
The information architecture was designed to support both high-level overview and detailed investigation workflows, ensuring users could quickly access the information they need at each stage of their work.
Design and Testing
Wireframing
Started with low-fidelity wireframes to establish layout and information hierarchy. Focused on creating clear visual hierarchy and ensuring key information was easily accessible.
Design Principles
- Clarity over complexity - Make threat data easy to understand
- Context is key - Always provide relevant background information
- Actionable insights - Every piece of data should support decision-making
- Consistent patterns - Use familiar UI patterns for security tools
Low-fidelity Prototyping
Created interactive prototypes to test core workflows, including threat investigation, email analysis, and threat intelligence exploration.
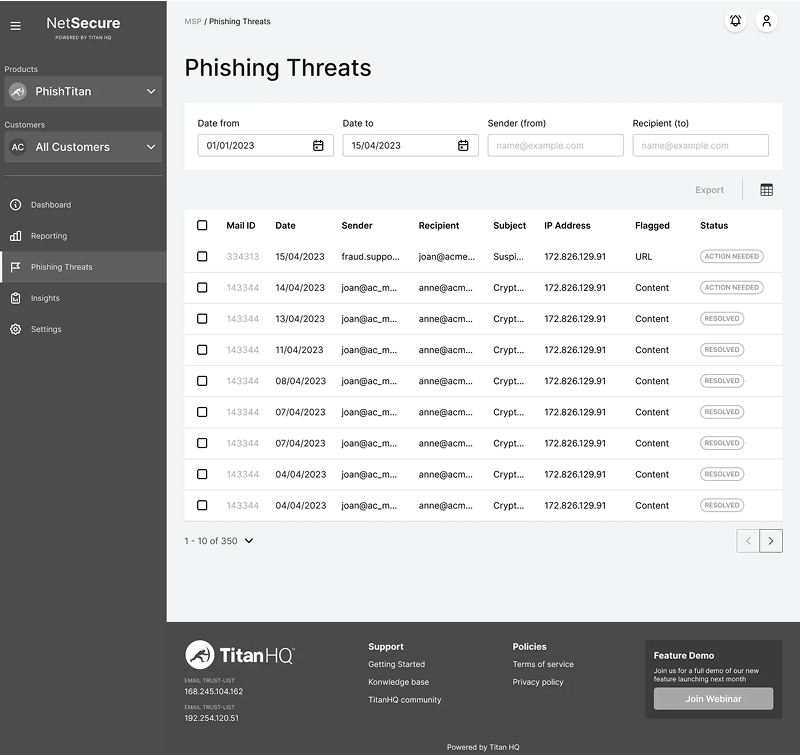
Usability Testing
- Conducted usability tests with security analysts and IT administrators
- Tested key workflows including threat investigation and email analysis
- Gathered feedback on information architecture and navigation
Findings
- Users needed more context when viewing threat details
- Navigation between related threats needed improvement
- Visualizations helped users understand patterns more quickly
- Email content view needed better organization of information
High-fidelity
Refined the design based on testing feedback, creating a polished interface that balances comprehensive functionality with intuitive usability.
Solution Highlights
- Comprehensive dashboard with key performance indicators and threat trends
- Detailed threat intelligence with geo-location mapping and threat type analysis
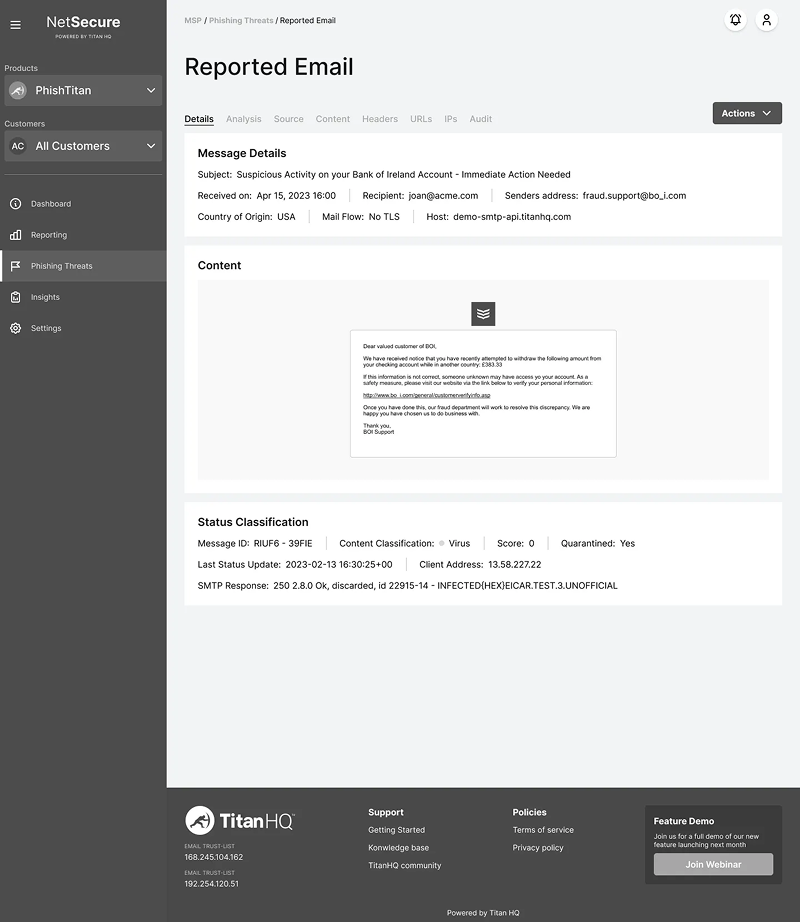
- Intuitive email analysis interface with clear organization of content, attachments, and headers
- Actionable insights that help users prioritize and respond to threats
- Unified platform that consolidates threat data from multiple sources
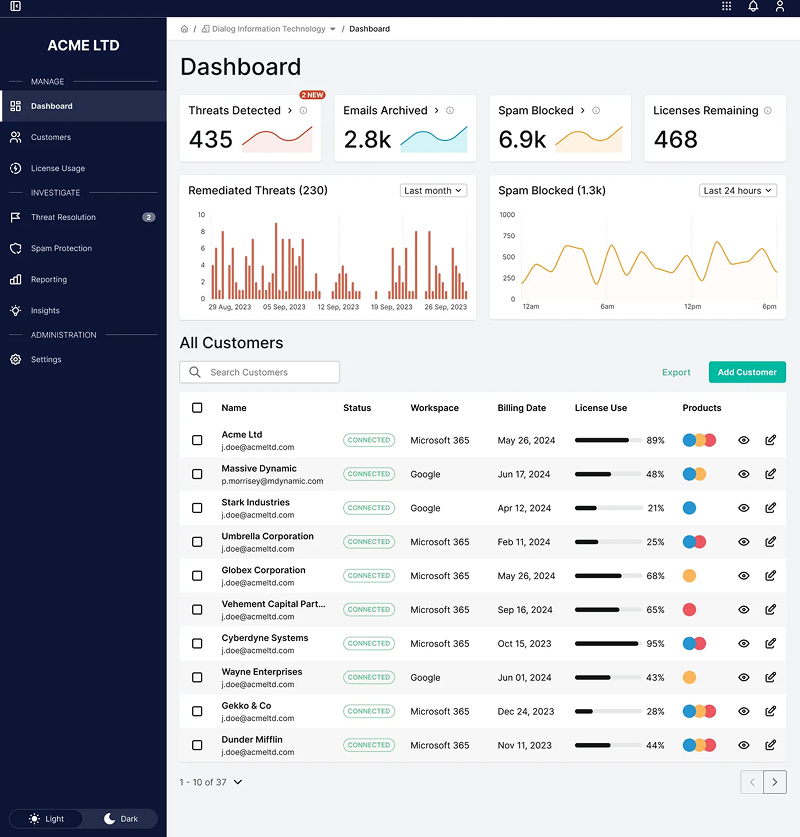
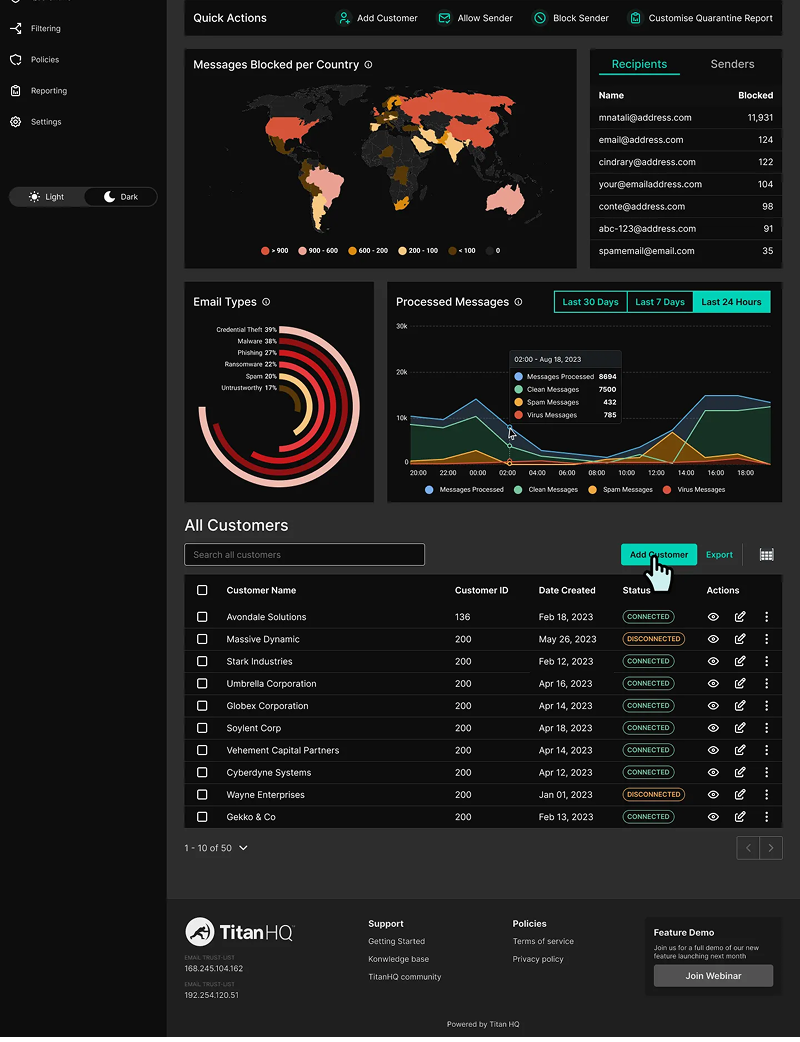
Impact
- Faster incident response through improved threat visibility and prioritization
- Improved user experience with intuitive interface and clear information architecture
- Better decision-making through actionable threat intelligence and contextual insights
- Reduced false positives through improved threat detection accuracy
I finally understand what the system is doing — and I can explain it to customers.
Let's connect
Shoot me a message here or connect with me on LinkedIn to get in touch.